Social engineering attacks remain a top concern for organizations and individuals worldwide in the ever-evolving landscape of cybersecurity threats. For IT departments, it is crucial to be aware of different types of challenges, and to help employees understand and prevent any risks. Here are some tips on how to boost your digital security infrastructure.
The human element
While technology plays a significant role in digital security, the human element remains a critical factor. According to the Verizon 2023 Data Breach Investigations Report, 74% of breaches involved the human element, which includes social engineering attacks, errors, and misuse. This statistic underscores the importance of educating employees about the various attack types and protection methods.
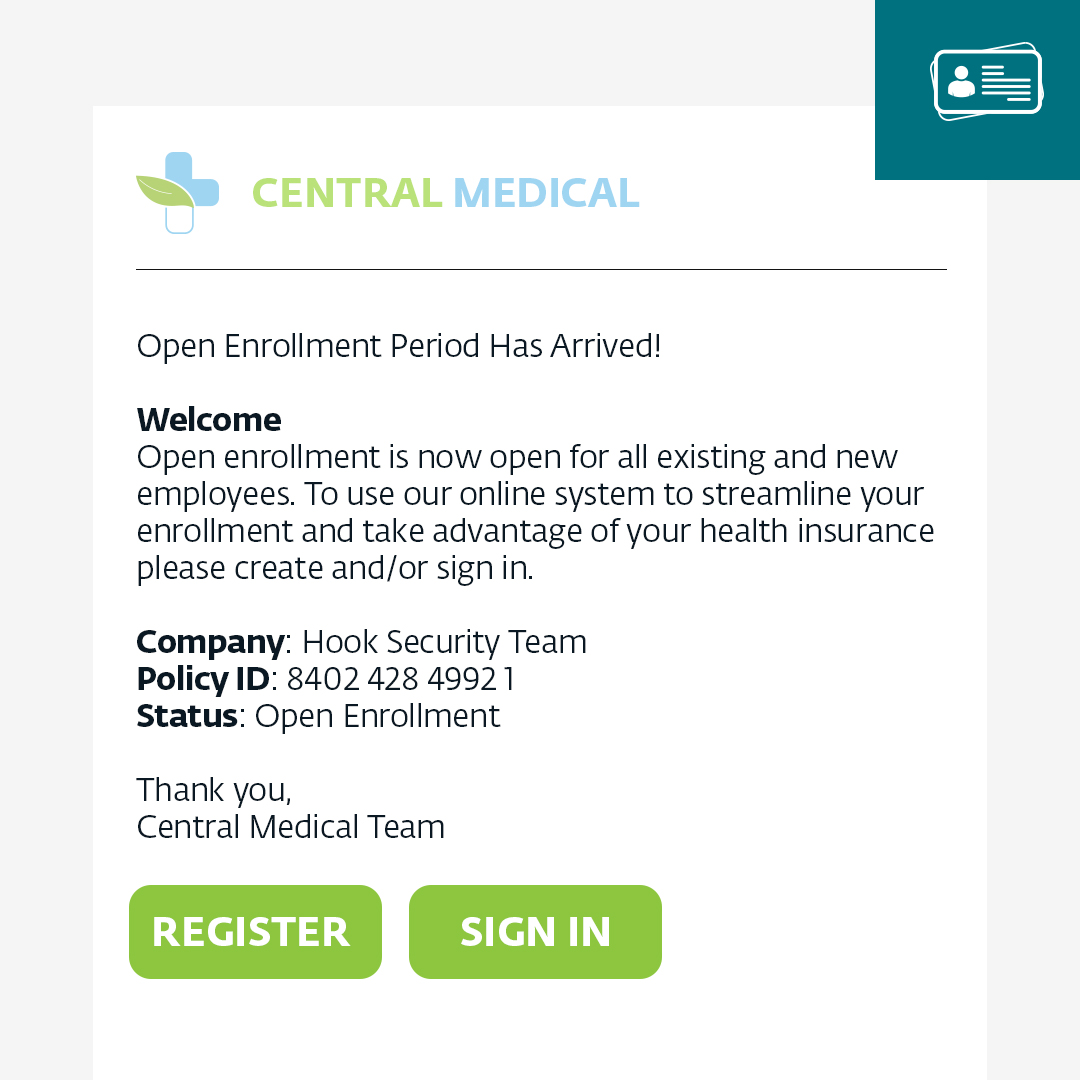
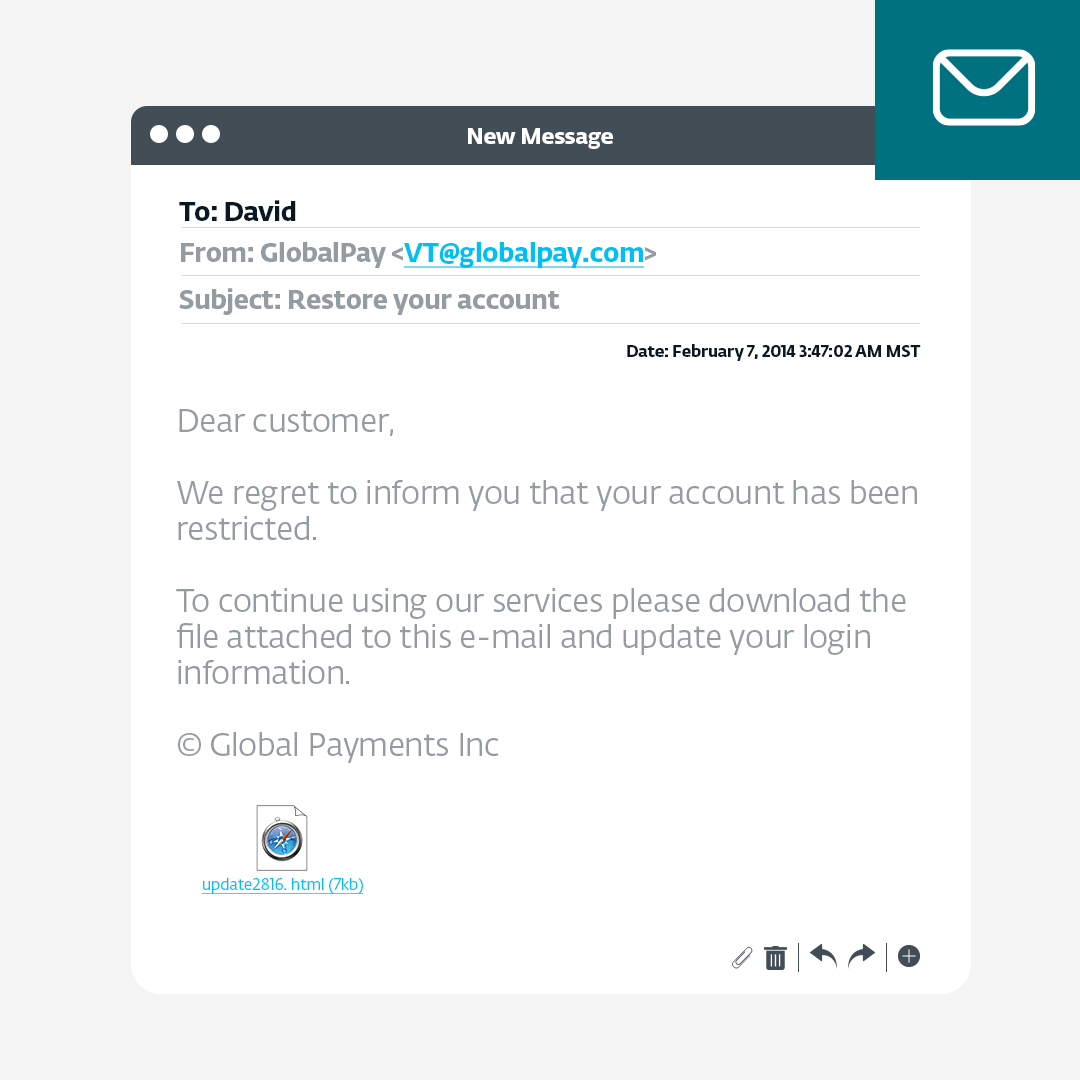
Probably everyone in your company has already heard about phishing, but that does not make it any less dangerous. On the contrary, phishing emails remain among the most prolific cybercrime techniques, where attackers attempt to deceive individuals into revealing sensitive information, such as passwords, credit card details, or personal identification, by posing as trustworthy entities. They typically use deceptive tactics, such as fake emails with links to websites that mimic legitimate organizations or individuals. As many might think, email isn't the only vehicle to deliver a scam, and lately, it has not been the most effective. Let's look at some other forms of phishing.
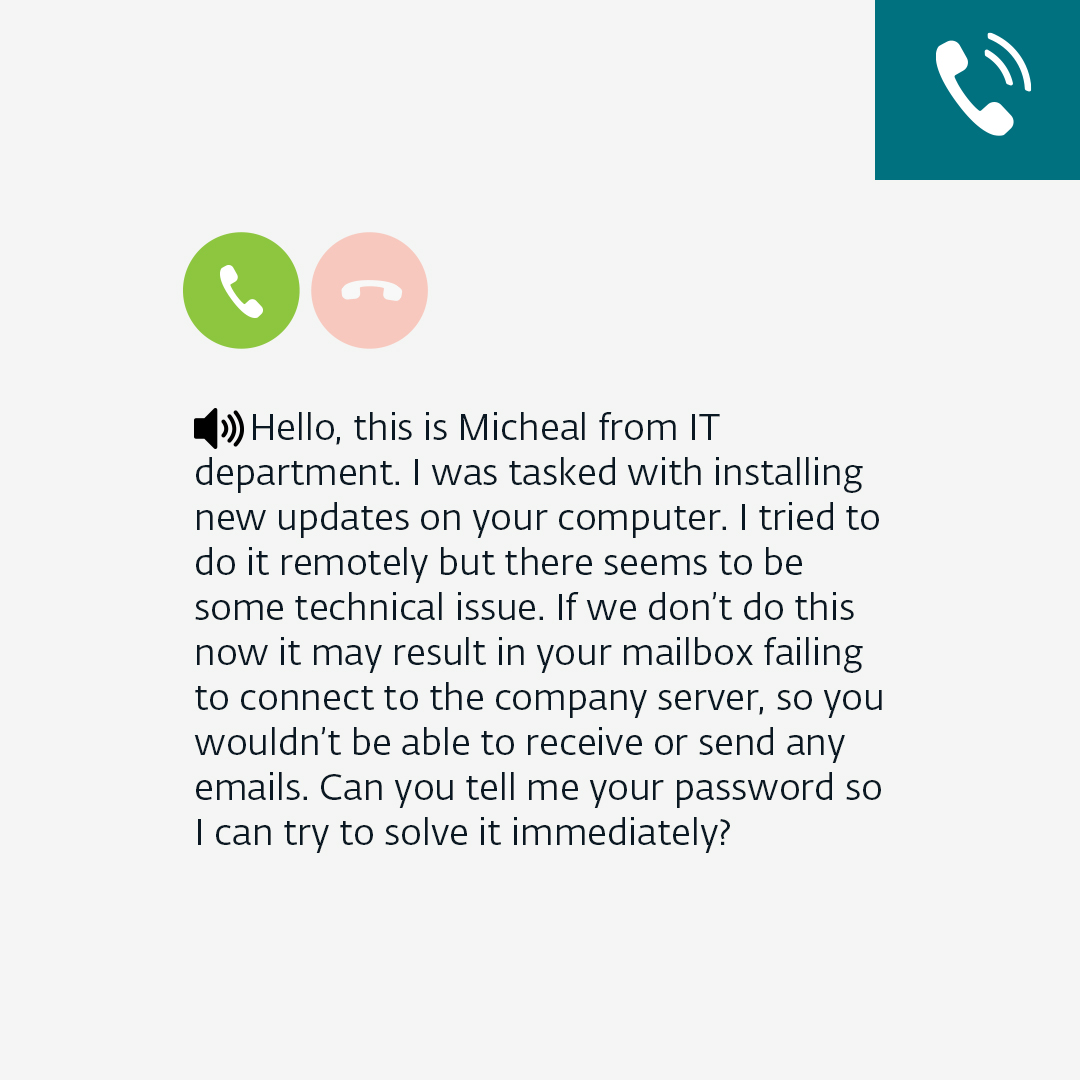
Vishing
Vishing, short for "voice phishing," involves scammers using phone calls or voice messages to deceive individuals into divulging sensitive information or making fraudulent payments. The sophistication of these attacks ranges from human impersonators to automated robocalls. Some scammers even employ call spoofing, using legitimate phone numbers to enhance their deception. The latest version of vishing includes deepfake calls, which can simulate a specific person's voice using AI tools, to make them even more convincing.
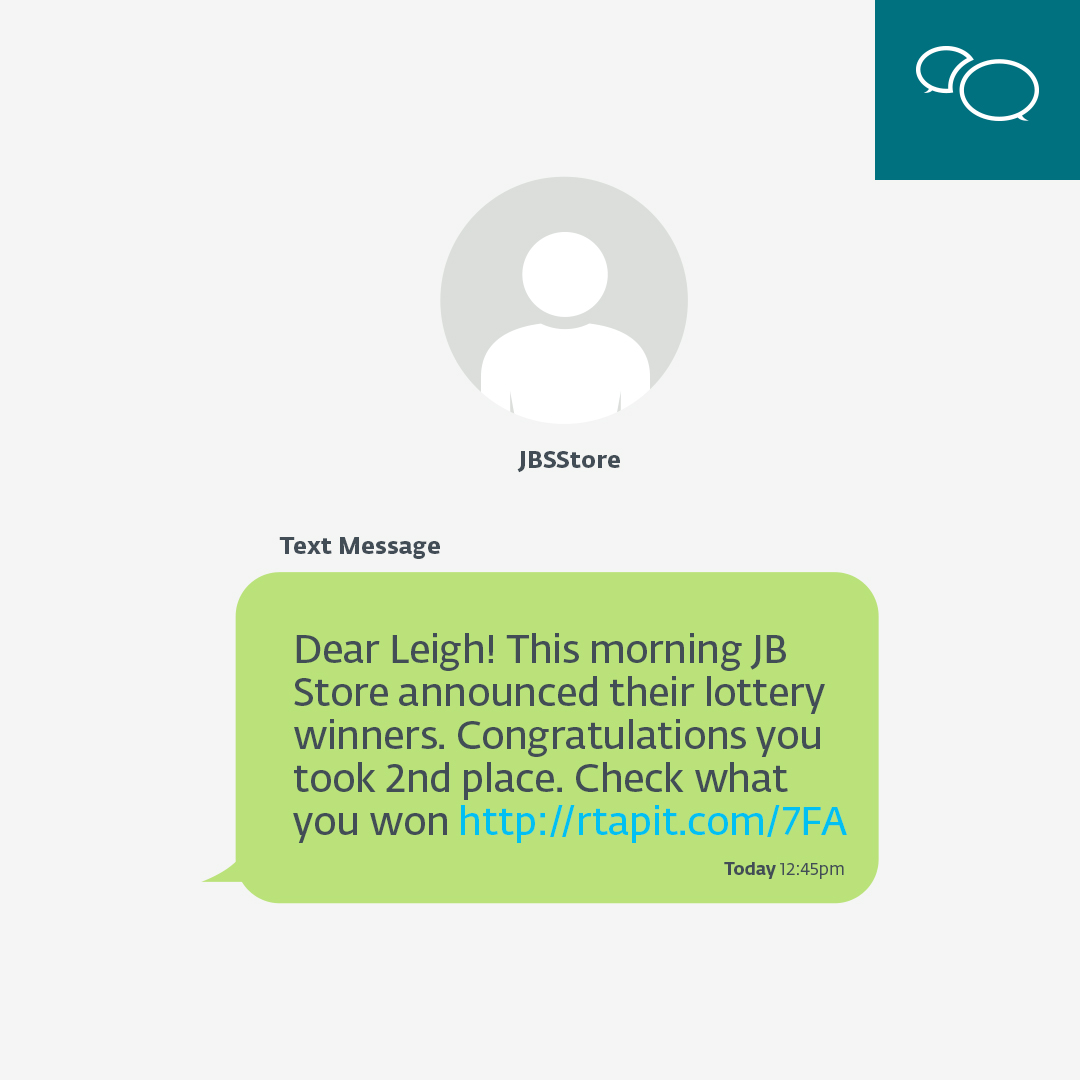
Smishing
Smishing, or "SMS phishing," means sending fraudulent messages via text or messaging apps to manipulate victims into performing specific actions. The messages typically contain links that direct recipients to malicious websites, login pages, or apps. Once accessed, these channels can extract personal information, including payment card details, or infect the victim's device with malware.
To effectively combat social engineering, keep common scams and their goals in mind:
Basic rules for employees
There are several good practices employees can adopt to protect themselves against various types of social engineering:
- Pause, think, and act: Scammers rely on the urgency to manipulate victims. Take time to evaluate requests, and avoid hasty actions. Avoid clicking on links in text messages, and visit the organization's official website to verify the communication's legitimacy.
- Be suspicious of unknown numbers: Verify calls or text messages from unfamiliar or suspicious numbers. Avoid disclosing any personal information or clicking unknown links within messages. This helps you minimize the chances of falling victim to such scams.
- Keep personal information private: Never disclose sensitive information such as account numbers, Social Security numbers, passwords, or Multi-Factor Authentication (MFA) codes to unknown individuals over the phone or in a message. Legitimate organizations would not request such details through unsolicited calls or messages.
- Verify identity: If you receive a message from someone claiming to represent a company or government agency, avoid interacting directly. Instead, independently verify their authenticity by contacting the organization using the official contact information available on their website.
- Enable strong security measures: Use strong and unique passwords to protect your accounts. Consider utilizing password generators and managers to create long and complex passwords or passphrases, and store them securely. Use Multi-Factor Authentication (MFA) whenever available to add an extra layer of protection.
Digital security awareness training is vital to protecting against cyber threats. Download the free Phishing playbook for employees, and share it with your team.