You have probably heard about social engineering – psychologically manipulating people into involuntarily revealing sensitive information. Let's take a look at impersonation, another non-technical attack technique used by cybercriminals pretending to be trustworthy people while trying to manipulate others (eg. to order and approve fraudulent transactions). How can you recognise when you're being contacted by a cybercriminal instead of your colleague?
Impersonation is defined as the practice of pretending to be someone else – in this case, in order to obtain information or access to a person, company, or computer system. To achieve these goals, cybercriminals use phone calls, emails or messaging applications, among other methods. In many cases, attackers choose names from the company's top management, and set up an email that looks as if it were written by a manager.
It is quite unbelievable how much corporate information is available on platforms like LinkedIn that disclose the company's structure and the names of its employees. An attacker can use such data to try and contact several employees from the company, asking them to carry out money transfers, pay invoices or send important data. That's why impersonation could be so dangerous for companies – these attacks could cause a data breach and financial loss.
According to TEISS, impersonation attacks targeting businesses of all sizes across the world rose by almost 70% in 2019, compared to the previous year.

Security solutions should protect from technical attacks. But impersonation techniques rely more on psychology – they take advantage of people's trust. Therefore, training employees on best practices of security hygiene is equally important. Here are a few tips that could help you and your staff reduce the risk of falling for social engineering methods, and filter out malicious content.
How to deflect impersonation attacks
1. Learn to recognise impersonation messages
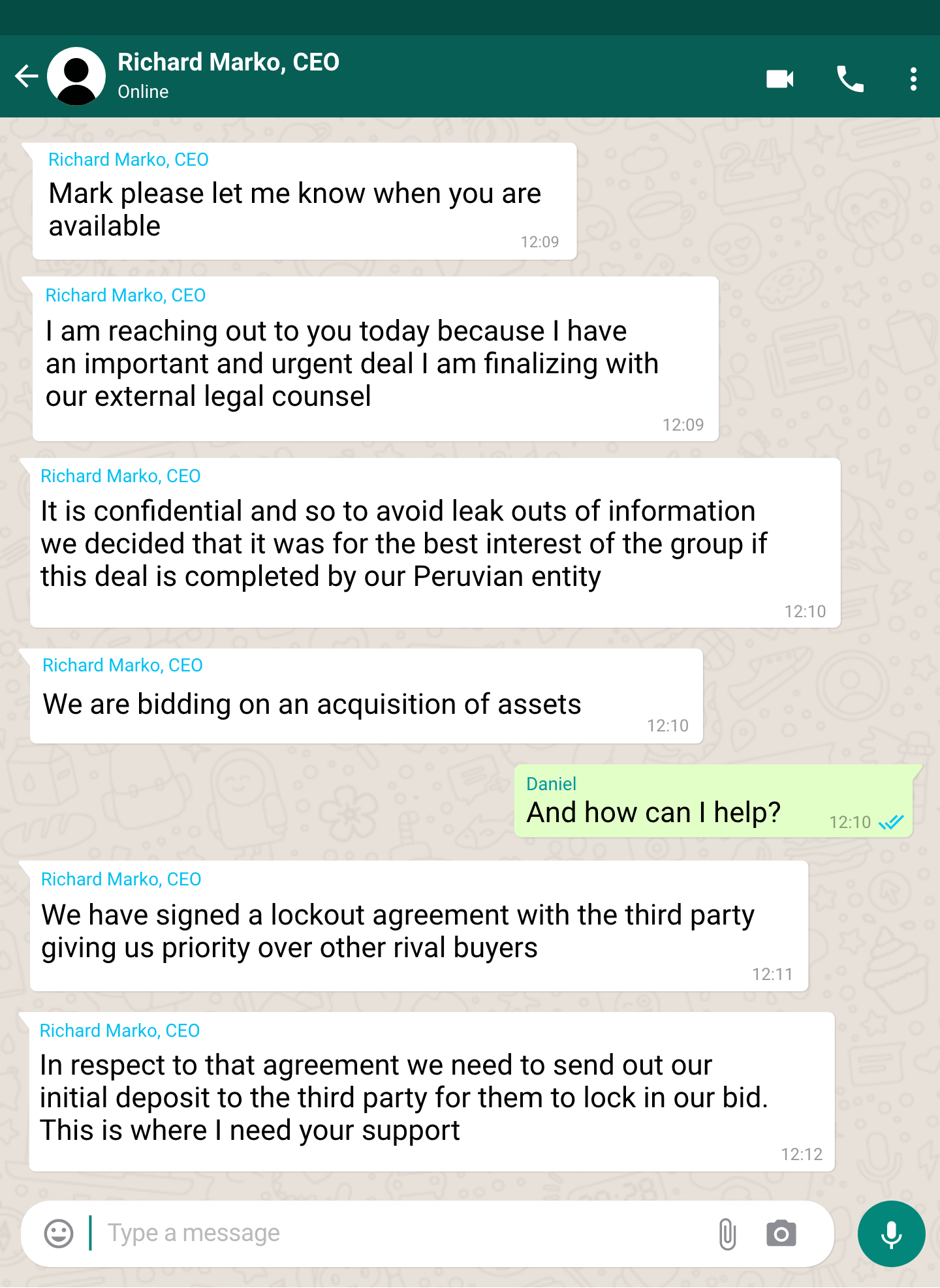
Remember, awareness is key. The more we know about impersonation attacks, the more we can avoid them. Let's look at how impersonation emails work. Many try to instill a sense of urgency and fear in their targets. That feeling leads victims to perform the desired task. This could involve something that you find unusual and suspicious, such as purchases that aren’t related to your business, with clients you don’t recognise. Cybercriminals also try to impose a short deadline for the required tasks.
Fraudulent messages often contain grammatical mistakes or incorrect applications of corporate branding. However, those are just the easier ones to spot. Attackers adept at advanced impersonation might manufacture an email message that looks very real, including an official employee photo or signature at the end of an email. So, even if the template seems legit, be cautious if you find the request in the message odd.
2. Think about the context
Sometimes we are too busy and we make decisions without much thought. Maybe it takes a few extra seconds, but you should always consider whether the email makes sense. Why, exactly, is this colleague asking just for this purchase or this sensitive personal information? Anything unusual that deviates from your company's traditional processes should be a warning sign. Even if the email apparently does come from a trustworthy individual, such as the CEO, it could be a fraud. Stay vigilant and verify any requests with other colleagues.
Sometimes cybercriminals may know that someone is out of the office, and act like they are covering for him or her. In that case, verify the information in question with their superior or coworkers. As the saying goes, you should “look before you leap.”
3. Check the email address
Receiving a business email from personal accounts? The email address could seemingly belong to someone you know, but it is always better to answer that person at their official email address.
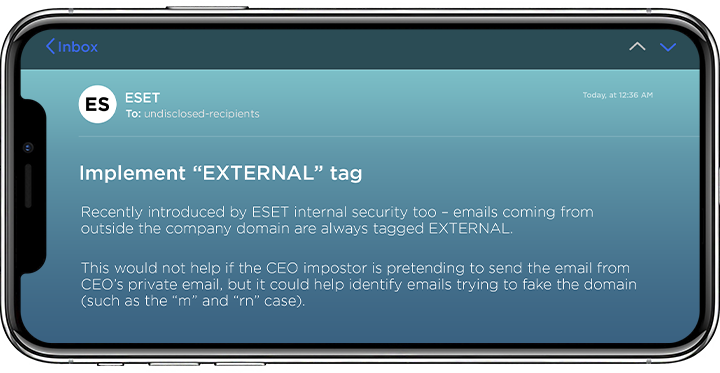
Also, sometimes, hackers can use an email that looks almost like an official corporate address at the first sight. But domain names could contain slight deviations. What are some of the most common mistakes in email addresses? Swapping the correct letters with others that look similar; for example, replacing “m” with “rn.”
4. Verify the person through another communication channel
Measure twice, cut once. Do you suspect the message you received is fraudulent? Give the sender a call or use other communication channels. However, email is not the only communication channel that hackers can use for impersonation attacks. You can also be contacted via messaging applications such as WhatsApp. If you have received a suspicious message on WhatsApp, you should write the person via a corporate email, or call them back.
Alternatively, you can also simply ask the person directly face-to-face. Don't worry about bothering someone, even when they might be busy. For example, you might be reluctant to disturb your CEO. That’s natural, because the higher a colleague’s position, the more hesitant we are to reach out to them, especially when they are out of the office. In that case that you can't contact your superior face to face, you can speak to their representatives or others you would expect to be knowledgeable about the situation. For example, a large, urgent overdue invoice payment surely would (or should) be known to your CFO or COO, so check with them. Remember – vigilance pays off.
The recommendations mentioned above may take extra time. But you can be sure that your investment will pay off when your business and work environments are under control and safer from cyberattacks.
Attackers might also choose to trick you to click on malicious attachment or link instead, so be sure to have a comprehensive security solution in place, which should detect and block this threat.




