Sextortion scams are a growing threat that can cause significant distress and damage to individuals and organizations. IT managers are crucial in ensuring that their teams are informed about these scams and are equipped to respond effectively.
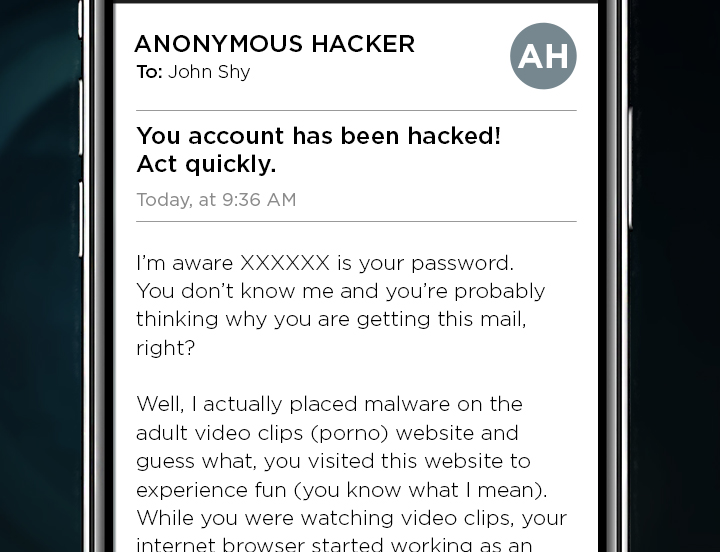
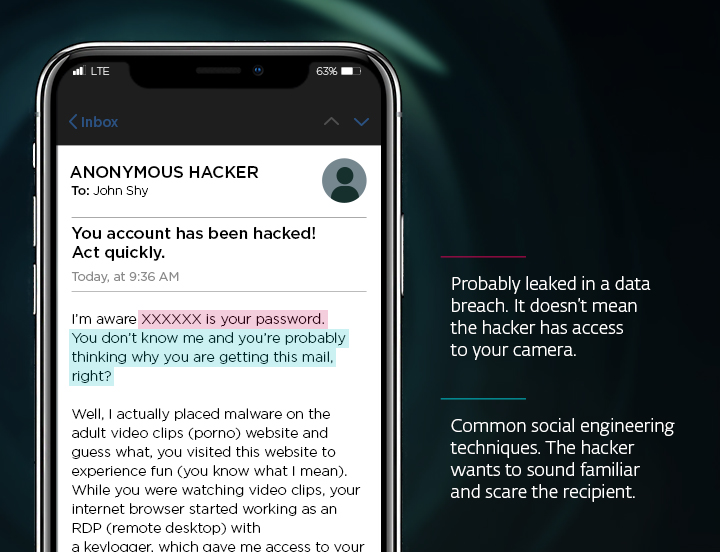
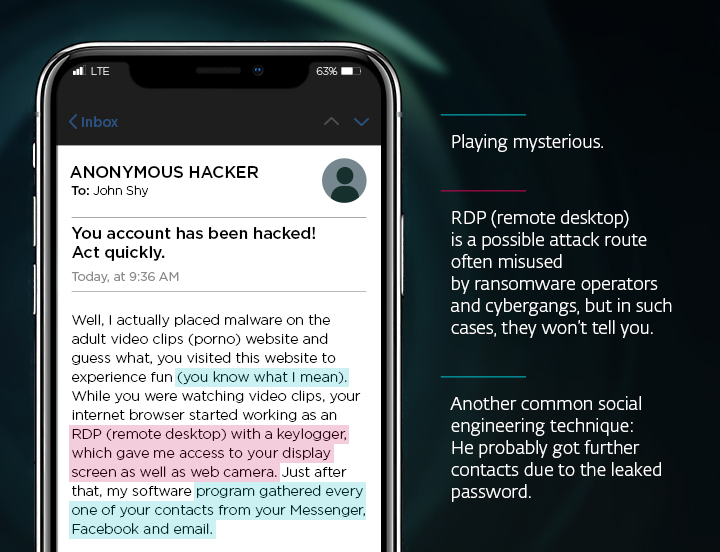
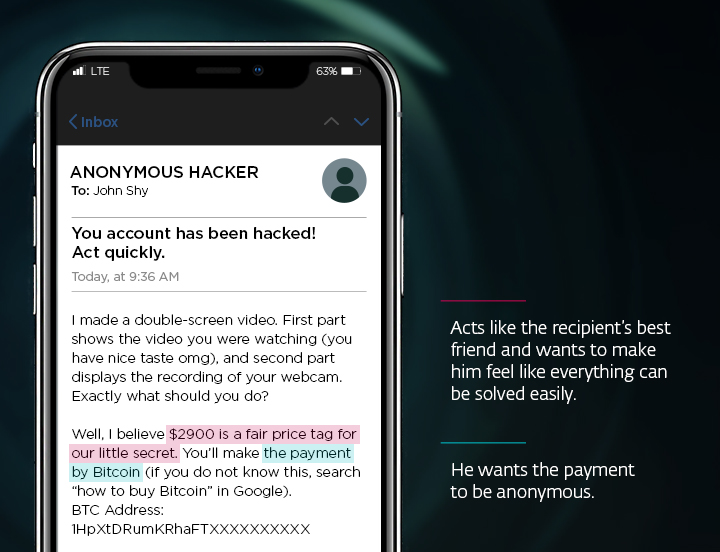
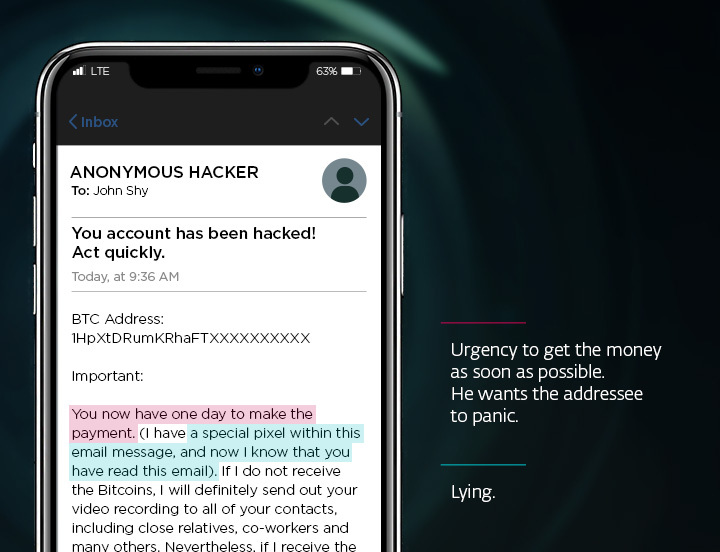
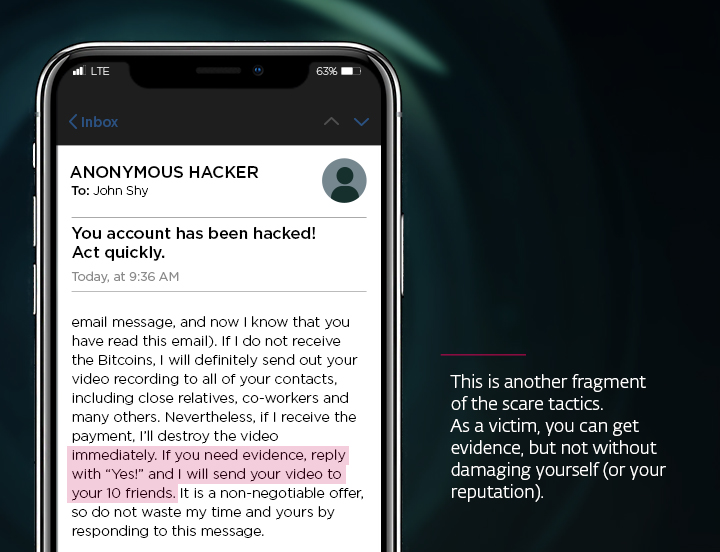
Sextortion leverages fear and embarrassment to manipulate victims into complying with the demands of cybercriminals. This typically involves an email or a private message containing false claims that the sender has compromising photos or videos of the recipient. Often, the mysterious blackmailer claims to have stalked the victim via their webcam while viewing some explicit content, for example. The threat is clear: Pay a ransom, or the embarrassing material will be shared with colleagues, friends, and family.
However, it is important to realize that the content of these emails is often wholly fabricated. Cybercriminals use intimidation tactics to create a false sense of urgency and vulnerability in their targets. These claims are often empty, and the scammers have no compromising material whatsoever.
The return of sextortion to the spotlight
Sextortion and other similar scams are on the rise, as modern technology is making it even easier for cybercriminals to commit them. In 2023, sextortion attacks have reached numbers not seen since 2021, becoming the third most common email threat. The FBI has also warned the public that cybercriminals can now easily use AI and deepfakes to transform ordinary photos into manufactured sexual content that can be used in sextortion scams.
The first line of defense against sextortion scams is awareness. Make sure your team is aware that:
Sextortion scams are on the rise: Emphasize that sextortion attacks have surged recently and become one of the most prevalent email threats.
AI and deepfakes are in play: Everyone, including cybercriminals, now has access to advanced technologies, which allow them to manipulate images and videos for sextortion scams to create convincing fakes.
What should employees do if they find a sextortion email in their inbox?
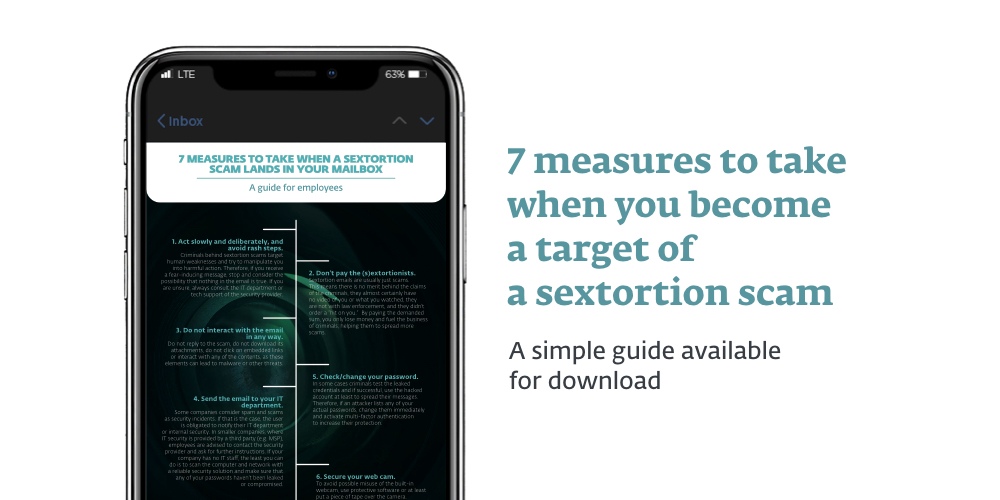
1. Take a moment to think. The content of the email may be completely false. Employees can contact IT or their security vendor for technical support if unsure about the received content.
2. Don't engage with the scam. Do not reply, download attachments, click embedded links, or otherwise interact with the content of the email. These actions could be a gateway for malware or other security threats.
3. Do not pay. Do not give in to extortion demands. Paying the ransom not only funds criminal operations but also provides no guarantee that the threat will disappear.
4. Notify the IT department. If a sextortion scam targets a work email address, the employee should notify IT support. They can help resolve the situation and scan the computer system for potential malware.
5. Change passwords as a precaution. If the attacker mentions having the user's credentials, it is safer to change them on all platforms and also use multi-factor authentication (MFA) wherever possible to increase the level of protection.
6. Collect all the evidence. If you believe you are the victim of sextortion, collect all evidence including usernames, email addresses, photos, videos, etc., and report it to the relevant office in your country, such as the Internet Crime Complaint Center (IC3) in the United States.
While sextortion scams are mostly swindles, extortionists try their best to get under the employee’s skin to scare them into paying the demanded ransom – usually in cryptocurrencies that are difficult to trace. Encourage your employees not to take social engineering scams lightly, but also not to panic when they receive a similar threat. Keeping a cool head is your employees' best defense.